AWS — cross-account access with IAM roles
Overview
The following guide provides a step-by-step approach for creating cross-account access using IAM roles. Prior knowledge of IAM concepts and the process of assuming roles is required in this guide.
Enabling cross-account access with IAM roles
To enable cross-account access, an AWS Identity and Access Management (IAM) role is created in the account (Account A) that owns the AWS resource which needs to be accessed. This role is granted specific permissions to access the resource. Then, the owner of the second account (Account B) can create a policy that allows a user or another resource in Account B to assume the role in Account A. When the IAM role is assumed, temporary security credentials are provided that can be used to invoke the resource in Account A.
For the case of API Gateway, the sts:AssumeRole action is used to assume the IAM role in Account A, which provides temporary security credentials. These credentials can be used to invoke the API Gateway in Account A from Account B.
Best guide to follow
Follow this guide which is the one I followed when our attempts finally worked:
Missing pieces
Some unmentioned things in the guide.
Protecting the API Gateway resource
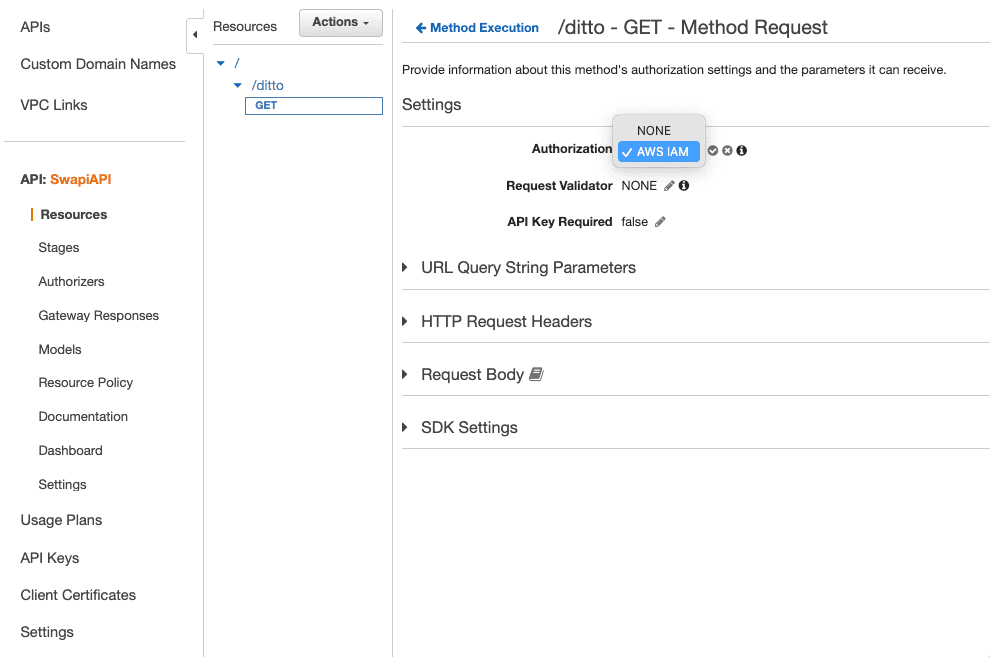
We enabled cross-account access, but the API Gateway resource isn't protected. To set the authorization method for the resource as AWS IAM, Go to the resource -> Method Request:
Deploy it after applying the above change.
Modifying the policy
After modifying the policy, you'll have to re-deploy your API in order for the changes to take effect.
Invalid resource ARN
Make sure the ARN for the resource in the trust policy is correct. If it's not correct, you'll get the following error message:
{"Message": "User: arn:<SOME_USER> is not authorized to perform: <ACTION> on resource: arn:<SOME_RESOURCE>"}